
When a security issue occurs or as part of security-related preventive maintenance, digital forensics software is used to investigate and examine IT systems. These tools assist organisations in conducting in-depth analyses of IT…
Read more
Access to a network of servers that can enhance website performance, content delivery, and application availability on an enterprise scale is provided by providers of enterprise content delivery networks (eCDNs). In order to…
Read more
Users of IoT device management software can manage, track, and track physical IoT devices. Using these methods, users can frequently remotely deliver software and firmware upgrades to devices. IoT device management software also…
Read more
Software development solutions geared exclusively at IoT developers creating IoT apps are known as IoT development tools. Integrated development environments (IDEs), command line interfaces (CLIs), software development kits (SDKs), libraries and coding frameworks,…
Read more
Real-time monitoring of an asset’s performance is accomplished via digital twin software, which offers a virtual representation or simulation of the physical asset. Ultimately, the asset is optimised for peak performance using these…
Read more
Industrial organisations can better plan, organise, and keep an eye on complex manufacturing and supply chain processes spread across numerous sites and teams thanks to connected worker platforms. This kind of software promotes…
Read more
Distributed denial of service (DDoS) attacks are globally protected against using cloud DDoS mitigation software. DDoS attacks flood websites with traffic, which is typically supplied by “botnets” made up of malware-connected networked endpoints….
Read more
Rentable computer servers that are fully managed and maintained by the service provider are available from managed hosting providers. The duties of on-premise server administrators, such as hardware setup and configuration, software installation,…
Read more
Managed DNS service providers give their clients access to computer resources and streamline their web traffic. These service providers combine data center resources to provide traffic across various customer networks, websites, and applications….
Read more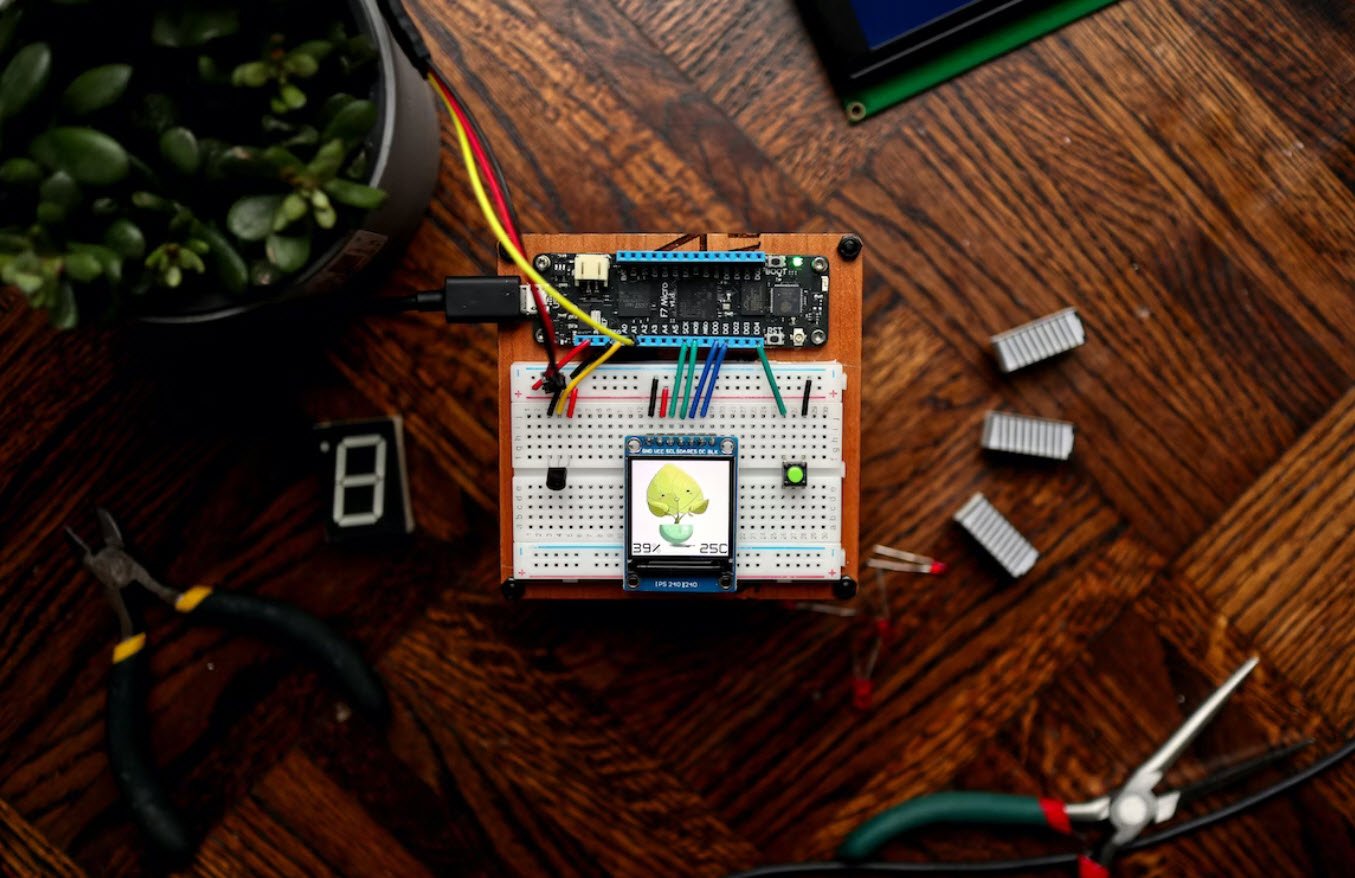
The Internet of Things (IoT) has revolutionized the way we interact with the world around us, enabling seamless connectivity between devices and systems. To harness the full potential of IoT, businesses and individuals…
Read more
Developers can create applications tailored for IoT uses using IoT platforms. These platforms allow users to develop, test, deploy, and iterate on IoT-specific apps quickly. Businesses can connect these applications once they’ve been…
Read more
IoT edge platforms help facilitate localized computer processing on IoT devices. These devices constantly analyze streams of data including information about networks, actions, and anything else the device is connected to or interacting…
Read more
